Every day we offer FREE licensed software you’d have to buy otherwise.

Giveaway of the day — CryptoBuster 1.0.9 Beta 2
CryptoBuster 1.0.9 Beta 2 was available as a giveaway on May 30, 2022!
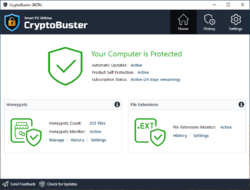
CryptoBuster is an effective anti-ransomware solution with a small system footprint that can work side by side with your existing security product to offer an additional security layer and form the last line of defense against ransomware to protect your valuable data from damage.
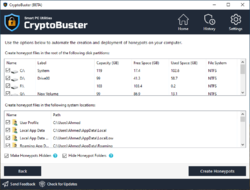
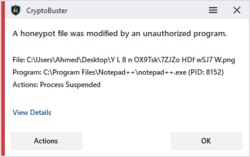
CryptoBuster uses honeypots, which is an efficient and proven technique with low false-positive chances to detect and stop ransomware when they start to encrypt user files. You have full control over the honeypots creation process as you can either create honeypots manually customizing their names and locations or you can leave this job to CryptoBuster that can deploy hundreds of honeypots in strategic system locations with custom names and file types designed to allow ransomware to target those files before they can reach any of your important files.
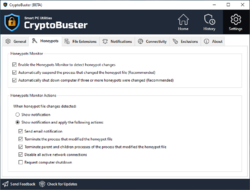
Besides Honeypots that are effective to stop ransomware when they start to encrypt user files, CryptoBuster can intelligently monitor the file system to detect malicious activities that may indicate an ongoing ransomware attack or sometimes indicate the preparations for an attack. For example, CryptoBuster can detect the creation of files with extensions that are known to be used by ransomware to encrypt user files, also you can configure CryptoBuster to detect the creation of potentially dangerous files like batch files and scripts that are commonly used in ransomware attacks, or even to detect the creation of files of unknown types which is an aggressive technique used to stop most of the ransomware strains that change file extensions.
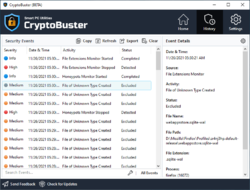
CryptoBuster was built to be a user-friendly and configurable anti-ransomware solution that is why it comes with a full range of tools and settings to allow you to customize all ransomware protection aspects provided by CryptoBuster and to have full control over actions made by the software. You can choose which protection module to enable and configure how this module works, configure automatic actions to perform in response to a specific event or disable this automatic response by setting CryptoBuster to monitor and report only. CryptoBuster comes with Security History feature that logs every security issue detected and actions performed by CryptoBuster; this would allow experienced users to understand how CryptoBuster works and the best way to configure the protection settings for best performance and user experience.
System Requirements:
Windows 11/ 10 (32-Bit and 64-bit); Microsoft .NET Framework 4.8
Publisher:
Smart PC UtilitiesHomepage:
https://www.smartpcutilities.com/cryptobuster.htmlFile Size:
12.1 MB
Licence details:
1 year free updates
Price:
$22.95
GIVEAWAY download basket
Comments on CryptoBuster 1.0.9 Beta 2
Please add a comment explaining the reason behind your vote.


First, I would like to thank everyone for trying CryptoBuster and my apologies to anyone who had issues with the software - please remember the software is in Beta, and your feedback and error reports are very important to improve and fix the software issues -
We would like to share with you some of the proposed features that will arrive in the upcoming CryptoBuster releases.
– The development of Windows Driver to intercept ransomware at the Kernel level.
– Support honeypots and file system monitoring in network shares - the first place where ransomware attacks-
– Startup locations monitor - prevent ransomware from achieving persistence -
– Data shield -a feature that only allows trusted apps to read/write to specific files, protecting data from both encryption and exfiltration -
We are open to discussing any feedback or suggestions.
Save | Cancel
Could never download the program. It indicated "Opening when complete" as usual, except it was never complete. It always indicated "27 minutes" as time remaining. I don't usually have problems downloading or installing software. Unfortunate experience. Sorry for both of us.
Save | Cancel
I have the setup program for version ver1.0.823 Beta but I did not have a Win 10 test machine at the time so I never installed it. Now that I have a Win 10 test machine, I was curious about the program, but when I browse to the folder that has the version 1.0.823 setup file, Windows Defender brings up an alert. The details are:
Misleading:Win32/Lodi
This program makes misleading or fraudulent claims about the files, registry entries, or other items on your PC.
VirusTotal.com reported 26 security vendors and no sandboxes flagged this file as malicious
The current version setup file does not trigger Windows Defender and it has a perfect score (all "Undetected") on virustotal.com:
"No security vendors and no sandboxes flagged this file as malicious"
The older version is from December 2021. This newest version is 5 months later. I can only guess that the underlying technology of this latest version has changed quite a bit. Can Smart PC Utilities elaborate?
By the way, thanks for a year of updates. I expect it would pointless without being able to keep up with the latest evolutions of this software.
Save | Cancel
Gary, The first CryptoBuster release (v1.0.823) was malware-free, and there were no major changes between the two app releases.
What happened is that an app certification entity named AppEsteem https://appesteem.com/ flagged CryptoBuster as misleading because they think the app has violated some of their deceptor rules, for example:
1.CryptoBuster has no option in the Settings that allows the user to shut down the app.
2. CryptoBuster is not notifying the user that it is running in the background after closing the app's main window.
3. The text in the CryptoBuster dashboard was misleading.
Using their relationships with major AV vendors, they reported the app to them, and AV vendors responded by flagging the app as malicious (Despite CryptoBuster does not contain any harmful or malicious code).
We contacted major AV vendors regarding this issue including Microsoft, but they didn't hear us.
To get rid of those false positive flags, we decided to fix the rule violations mentioned by AppEsteem and submitted the app to them for a review; they were cooperative enough to remove CryptoBuster from their deceptor apps list https://customer.appesteem.com/deceptors
Rest assured that the two CryptoBuster versions besides our other products are 100% clean.
Save | Cancel
After running I get message: "Unable to communicate with the CryptoBuster service" and the software is stopped.
What should I do?
Save | Cancel
Jerzy,
Firstly, I would like to deeply apologize for any inconvenience this issue may have caused.
Regarding the error “Unable to communicate with the CryptoBuster service.”; this may be due to an unhandled exception that occurred when starting the CryptoBuster service, or the software installer was unable to create the service in the first place.
Please make sure that there are no errors that occurred during the software installation, and that your anti-virus software did not interfere with the CryptoBuster installer.
Follow the steps below to help investigate and fix this issue:
1. Make sure that the CryptoBuster service already exists on the system by using the following command in the CMD:
sc query cryptobustersvc
If the service was successfully installed, there would be information related to the service, otherwise the error message “The specified service does not exist as an installed service.”
2. Make sure that your anti-virus software is not blocking CryptoBuster.
3. Enable the CryptoBuster Debug Mode that will give us more details about this error:
a. Terminate any CryptoBuster processes.
b. Download and execute the following Registry file to enable the CryptoBuster Debug Mode https://www.smartpcutilities.com/files/cryptobuster-debug-mode.zip
c. Start CryptoBuster, and after the error message close the application.
d. In the File Explorer, navigate to "C:\ProgramData\Smart PC Utilities\CryptoBuster\Logs".
e. Send us all the generated log files (Via support ticket or support@smartpcutilities.com).
4. Get more error details from the Event Viewer
Use the following CMD command to export all events related to CryptoBuster to "D:\cryptobuster.evtx"
WEVTUtil export-log Application "d:\cryptobuster.evtx" /q:"Event[System[(Provider[@Name='CryptoBuster'])]]"
Send us the evtx file (Via support ticket or support@smartpcutilities.com).
Save | Cancel
Block ports 139 (NetBIOS), 445 (Server Message Block), and 3389 (Terminal Services). These are the ports that APT29 uses. APT29 is the Russian hacking group that is causing much of the ransomware attacks. You're wise if you block these ports on your machine(s).
Save | Cancel
After installing
Unable to communicate with the Cryptobuster service
What should I do ???
Save | Cancel
Paweł,
Firstly, I would like to deeply apologize for any inconvenience this issue may have caused.
Regarding the error “Unable to communicate with the CryptoBuster service.”; this may be due to an unhandled exception that occurred when starting the CryptoBuster service, or the software installer was unable to create the service in the first place.
Please make sure that there are no errors that occurred during the software installation, and that your anti-virus software did not interfere with the CryptoBuster installer.
Follow the steps below to help investigate and fix this issue:
1. Make sure that the CryptoBuster service already exists on the system by using the following command in the CMD:
sc query cryptobustersvc
If the service was successfully installed, there would be information related to the service, otherwise the error message “The specified service does not exist as an installed service.”
2. Make sure that your anti-virus software is not blocking CryptoBuster.
3. Enable the CryptoBuster Debug Mode that will give us more details about this error:
a. Terminate any CryptoBuster processes.
b. Download and execute the following Registry file to enable the CryptoBuster Debug Mode https://www.smartpcutilities.com/files/cryptobuster-debug-mode.zip
c. Start CryptoBuster, and after the error message close the application.
d. In the File Explorer, navigate to "C:\ProgramData\Smart PC Utilities\CryptoBuster\Logs".
e. Send us all the generated log files (Via support ticket or support@smartpcutilities.com).
4. Get more error details from the Event Viewer
Use the following CMD command to export all events related to CryptoBuster to "D:\cryptobuster.evtx"
WEVTUtil export-log Application "d:\cryptobuster.evtx" /q:"Event[System[(Provider[@Name='CryptoBuster'])]]"
Send us the evtx file (Via support ticket or support@smartpcutilities.com).
Save | Cancel
Wouldn't let me register. Removed.
Save | Cancel
george McGrath, What error message appears when you try to register the software?
Save | Cancel
Sorry, we could not find a license associated with this email address
Save | Cancel
Port 139 is utilized by NetBIOS Session service. Enabling NetBIOS services provide access to shared resources like files and printers not only to your network computers but also to anyone across the internet. Therefore it is advisable to block port 139 in the Firewall.
Save | Cancel
Once installed, is there a way to test it to see if it actually works?
Save | Cancel
Wahtsup,
I guess you could try changing the name of one of the "honeypot" file created, or try changing the extension of a regular file to see if the software let you do it...The idea of this software seems appealing to me, but if it is working then all antivirus softwares should use that solution, should'nt they ?
Save | Cancel
Wahtsup, Test CryptoBuster on a VM, create honeypots then try to modify them manually or by using other tools and scripts, you can even run ransomware samples and see how CryptoBuster responds to it and how many user files were affected by the ransomware before CryptoBuster could halt it.
Save | Cancel
How it works internally I wonder ? From my knowledge ransomware is form of a rootkit, which operates on low level by hooking APIs working with files and encrypting/decrypting doing there - meaning from windows everything looks pretty much normal, until hook is removed - only then encryption is visible, right ?
So this 'buster' is something like 'Unhackme' or similar software hooking itself even somewhere lower (as dangerous as it sounds, makes it pretty much rootkit itself!) or it is just 'monitoring' windows file API activities (as useless as it sounds for finding ransomware) ?
Save | Cancel
dex, Not all ransomware are rootkits; most of them run in the User Mode which makes all their malicious and encryption activity visible to the OS and other apps. The current CryptoBuster Beta can only monitor and respond to IO activities made to honeypots or other file types monitored by the File Extensions Monitor. When a malicious IO activity is detected, CryptoBuster will respond with a variety of actions configured by the user. Those actions aim to halt the ransomware encryption activity, thus minimizing the damage.
Please be informed that CryptoBuster is designed to work with other security apps, so it can't offer full protection against ransomware by itself.
We are working on a file system driver for CryptoBuster that will not only allow CryptoBuster to monitor and respond to malicious activities, but it would allow the app to intercept and prevent honeypot modifications and other IO activities at the Kernel level.
Save | Cancel
Smart PC Utilities, Ok, fair enough, seems like you know what you do. I will try and test myself. BTW kernel mode is not always needed to hide malicious IO activity, better malware can effectively hide its presence or activity on filesystem even from user mode, its all about details and how extensive hooking is. Its always cat and mouse game. Probably most of retail users will not catch very advanced malware types, only those simpler spreading in the wild, so IO monitoring may be sufficient.
Save | Cancel
TK, yes, exactly, that is what really advanced malware does - utilizing ring 0 driver to hide all signs of presence of ring 3 process hooking (call-backs chain) all sorts of windows provided APIs to work with files etc - so nobody monitoring such APIs will see anything. From Windows API point of view file was never touched, despite internally being already touched and encrypted, but hidden ring 3 process serves it further to callbacks chain as 'original' untouched and decrypted.
To detect such behaviour is very difficult, one needs some antirootkit and deeper knowledge of api tables etc. But hopefully this kind of malware is not so common, pure ring 3 attacks originated by some exploits in web pages are simpler, and touching some honey pot files can be monitored.
Catching already escaped culprit is another story, but knowing fast that house is on fire may be valuable too, at least there is time to ask for professional help before ransom is demanded...
Save | Cancel
TK, CryptoBuster relies on Event Tracing for Windows (ETW), a Windows built-in kernel-level tracing feature that logs kernel events and by using CryptoBuster algorithms it will be filter those events to determine which events are considered malicious (e.g.: honeypot file modifications, creation of files with extensions known to be used by ransomware, creation of potentially dangerous files like batches and scripts) after that it reports this to the user and performs a series of actions configured for this type of event by the user.
If an IO event is happening in the Kernel, CryptoBuster will see it.
That is why we are working on a file system filter driver to prevent and halt ransomware modifications at the kernel level before reaching any of the user's real files.
Yes, the example applies to the current Beta version but CryptoBuster will help you retrieve the horse before it's too late.
CryptoBuster adds additional protection besides the default Windows security ransomware protection; use the honeypots wizard to select locations other than locations monitored by Windows security, CryptoBuster will create honeypots with custom names, types, and sizes tailored for each location aimed to attract ransomware before reaching any real files.
Save | Cancel
Smart PC Utilities, thanks for more detailed explanation. Interesting approach, events are often omitted in covering part of malware, so definitely worth a try.
Save | Cancel
TK, CryptoBuster does not need to write ETW events to a log file for filtering purposes as it consumes those events in real-time. Causing excessive writes would defeat the idea of CryptoBuster to be a lightweight security add-on.
From Microsoft Docs:
"You can consume the events in real-time or from a log file and use them to debug an application or to determine where performance issues are occurring in the application."
Ransomware accessing the drive directly to manipulate data would be challenging to detect and prevent even for sophisticated security solutions, however, I didn't see any ransomware utilizing its own file system drivers to manipulate files.
Regarding the Windows security Controlled Folder Access, it's a great feature to prevent ransomware and other malicious apps from modifying your files. We have an idea that is similar to the windows ransomware protection with additional features to address some of the Controlled Folder Access shortcomings:
1. Prevent un-trusted apps from both reading and writing to the files; this would help prevent data exfiltration, which is a common practice in ransomware that uses double and triple extortion.
2. Automatically allows apps with specific criteria from manipulating the protected folders without the need to add them manually to the trusted apps list (for example apps with valid digital signatures)
3. Improve user experience, by adding options to allow users to trust app and/or allow access to the file within the notification window itself; in Windows Security will you need to exclude apps manually using the Controlled Folder Access settings UI.
We used the word Crypto to refer to ransomware that uses cryptography to encrypt and damage user files, not the cryptographic systems themselves, and the word Buster to describe the purpose of our software which is to detect and stop ransomware activities to prevent damage or at least minimize it.
Save | Cancel
The Windows Installer Service could not be accessed. This can occur if you are running Windows in safe mode, or if the Windows Installer is not correctly installed. Contact your support personnel for assistance.
Save | Cancel
Alireza, Check the Windows installer service by using the following command in CMD (Administrative privileges required)
sc qc msiserver
Make sure the START_TYPE is set to 3 (DEMAND_START)
After that, start the Windows installer service with the following command:
sc start msiserver
Save | Cancel
krypteller, As CryptoBuster is intended to work with your primary security solution to form the last line of defense against ransomware. Your security solution is responsible for preventing and removing the malware in the first place, but in case of a new/ sophisticated ransomware strain that bypassed your security app, CryptoBuster will kick in to protect your data from damage or at least minimize the damage.
Regarding comparing CryptoBuster with a speedometer, it will show you how fast you drive, and at some point, it will slow you down or even force the car to stop to protect you from harm.
Save | Cancel