Every day we offer FREE licensed software you’d have to buy otherwise.
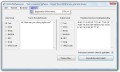
Giveaway of the day — Text Conversion Software PRO
Text Conversion Software PRO was available as a giveaway on April 30, 2008!
This software is great text conversion software. It allows to easily convert from text to hex, hex to text, binary to text, text to binary, and ascii to text or text to ascii, urlencoding/decoding and base64, octal to text and more!
Plus you can select a number of files to process automatically in batch (batch text conversion), and specify a default filename extension, or simply input some text into a text box and convert that way.
System Requirements:
Windows 95/98/2000/XP/Vista
Publisher:
HotHotSoftwareHomepage:
http://www.hothotsoftware.com/textconversionsoftware_software/File Size:
1.99 MB
Price:
$49.95
Featured titles by HotHotSoftware
Create a list of random numbers using this great random number generator! You can specify minimum and maximum ranges of numbers that you would like to generate. Choose the number of random numbers you would like to generate (100,000). Choose whether or not to include only unique random numbers.
This is great software to append 2, a few or multiple PDF files together. Simply select the PDF files you want to merge, and click on the start button! Add multiple PDF Files to merge from multiple/different directory locations, sort the order of PDF files with arrow buttons, fast and speedy joining of PDF files.
Using this software, you can easily and automatically find and replace text in a single, multiple, or selected files using simple or regular (regex) expressions. To start, simply select a file, any number of files, or recursively scan directories with wildcards. Then, you can enter multiple find/search and replace statements and order them how they should act on the file. (You can even save these set of instructions to use later, as a batch job on a set of files).
Find and remove duplicate mp3 files using this duplicate mp3 file finder! Recursively search directories for identical mp3 files to delete and send to the recycle bin, apply a checksum and check against checksums for mp3 files, match certain criteria within mp3 files, when available (i.e., comparing mp3 files against audio data size, approximate number of frames size, song length), and view mp3 details such as the mp3 header location, length of the song, the size and audio data size.
Comments on Text Conversion Software PRO
Please add a comment explaining the reason behind your vote.



Fifty bucks? Fifty bucks that could be spent on something actually useful or fun? Fifty bucks for something that does exactly what this free online website does?
http://www.paulschou.com/tools/xlate/
That's pathetic. I wouldn't pay a cent for this when there's a number of free utilities and websites that serve the same purpose.
guest32b: We've had enough 'heroes' like yourself around here that say "it's free don't complain!". We have full right to, thank you very much. Also, the reason that we can give thumbs-downs and thumbs-ups is the fact that not everyone is going to get here on the give away day, and if someone considers paying for it, they can read what others think of it.
From me, this software gets a 0/10.
Save | Cancel
:) Thank you very much, John! I'm not a programmer, so when I occasionally need to convert text, I don't want to have to strain my brain to recall a part I learned 5 yrs ago & have seldom used or never used, just to finish something that at times may not even be very important to me, but is to someone else. Not everyone here is a pro at everything in the world like some of above comments lead one to believe. There are some pros who come here, but many of us are just plain people. So again, I thank you so much for this, & for all your attention to this comment column too. :)
I did actually have a program in mind that I can't find anything online even partly similar to, just a couple weeks ago, & tried to find the page here where someone had said "let me know if you have a program to suggest". Will try to remember what my suggestion/request was, & will contact you when I recall it. lol:) Am on cold meds today, so my brain is half asleep. lol:)
Save | Cancel
@John #70:
Hi John. I appreciate greatly that you, as a maker of this software, did join the discussion. I reallize the discussion will not always please you. But my intensions are NOT to bash the programmer. I do try to address real issues.
In your comment #64 I quote:
"...the software that I use to protect it does, more specifically, it uses it prevents ‘hackers’ from (easily) reverse engineering the software. As an aside, a number of programmers/software developers use that software, and that company is still in business doing extremely well."
I understand from that that the functionallity was coded by yourself and that you did use some thirdparty software to protect your software from reverse enginering.
I do think you did a fine job of programming, all works flawless, nothing wrong with that at al.
The functionallity is a bit too common though to expect a great market for it is my guess, because of all the alternatives and the price (see my first comment #14).
The code injection must be part of the thirdparty software and believe me this will do you no good.
I hope I will be helpfull to give some recommendations here:
1] get rid of the nagg-screen in the software you provide. You can try to force people to stay honnest, but you should not force people to do things they dont have to and don't want to.
2] Use something different to protect your software. Something free of code injections.Perhapse UPX could do the trick for you: http://upx.sourceforge.net/
Your executables will be compressed, easier (smaller) to download but very hard to reverse engineer.
3] You might even turn this conversiontool into freeware (I don't think your loss will be too substancial) in order to make people aware of your site and do some more business.
What could be wrong with the protection software you use:
There are people making software just to lure people into a scheme of mal intentent. (here the example gets to be fiction) They might make freeware available that drop components vulnarable for code injection. When people use it it starts spreading around the world., aswell as the vulnarabilities do.
It abuses in that way people that only have good intentions.
Note: This has nothing to do with the GAotD-wrapper; nothing wrong with that.
I do think (again a matter of trust) you do have good intentions (as does GAotD; I never doubted that). Your showing here does that for me and the fact that you got the possibility to be a GAotD. So you might be unaware of all the components in the software on your site and it's dark potentials.
Thanks for your suggestion to use a second computer. I do use one of the former giveaways though "Returnill". I'm a really big fan of it. Don't worry, this keeps me on top of it.
Save | Cancel
Between Notepad++'s Hex Editor Plug-in (or many other calculators in free editors)and http://www.paulschou.com/tools/xlate/ is there any real point to using this software?
Save | Cancel
I find your conversion utility to be useful for what it is I do. Why jam your head with an unnecessary bunch of calculations. Free your mind to work on the more creative aspects of the project. Played around with it this afternoon and highly recommend it. (if it were FREEWare !$!!?) It wuld make more sense
Got some data you want to hide n plain sight? Obfuscate it!!!!
Surv_Tech
Save | Cancel
People, it's free today! So you won't pay that much for it usually, but you didn't, it was Free! At least it works, and you got something you might need to use in the future. I actually think it is a handy little program. I wouldn't of bought it for the price, but hey, free. Thanks
Save | Cancel
Before you download "Z Brain Upgrade" or pay for #43's "Z Brain is a Terrible Thing to Waste", please consider my encryption obfuscator, now in production as a not ready for prime time beta. It's compact, it has a tiny ensemble of plug-in skins in dress white or corinthian leather, and the embedded island music makes you think you're on a fantasy island instead of at work.
It's called Z Brain Boss Z Brain.
Save | Cancel
Im sorry to say giveawayoftheday, this product is pointless, who would need to convert that kind of humble jumble!
3 Bad Product in a row, get some that are quality please!!!!
Save | Cancel
I haven't programmed for years but I think in under 10 mins could easily write a program that does this if I even had a need for it...So their is no point in purchasing it especially at that price....But thanks anyway GOTD, keep up the good work
Save | Cancel
Is that why your DNS registration is anonymous and your street address is a Mailboxes Etc? Trying to cut down on the junk mail?
(Are you actually in Vancouver or are you really in Hothot? Btw if you are you get full marks for a pretty good pun with the company name)
Save | Cancel
Being a network guy (all IP address masking is based on binary), I find myself having to convert from decimal to binary quite often. How could this program not even have decimal to binary conversion?
Save | Cancel
Convert just about anything to anything else online by means of
http://www.onlineconversion.com/
Save | Cancel
#57 On the contrary, I think GAOTD is a great place for software developers to ask what potential buyers would like to see. Besides visibility for a given product that could be passed on to potential buyers, what else do you think developers get out of offering their software to us here for free? They get valuable feedback and suggestions on how to make their software better. Also, statements like "that doesn't do anything for me, but I would love to see THIS."
Sorry for not commenting on the software...I do not have a need for this.
Save | Cancel
@mic #58:
Some things can be used in a beneficial way and also in a bad way (like the knife I refered to earlier). Of course this does not mean that you should never use it, I mean in a beneficial way that is.
But it does mean you should be careful with it. Would you for instance trust a child playing with that potentially beneficial knife.
Ofcourse you're entitled to your opinion as I am. It has much to do with trust hasn't it.
Code Injections are infamous for using exploits. Even though these exploits might not even be deliberate. On the other hand using a deliberate code injection in your own programs has very few to do with using exploits (some spyware does work that way; using exploits from wellknown vulnarable software components). Deliberate code injection in your own programms has to have a very special reason to do some pretty special things.
Why should anyone use it in a nagg-screen forcing (that's not nice either) you to give your emailadres away together with all kind of control-captures to let you no escape ??!! I don't surely trust that !! I don't know about your Nirsoft, but I didn't say that there was something fishy about that as well. It all very much depends on the situation.
But you do trust it, be my guest by all means. I trust my virusscanner. Ofcourse you might say now that my virusscanner found a false positive (ofcouse also possible), but how would you know. This kind of reasoning would make using a virusscanner pointless. Then you just have to trust by heart software from Nirsoft but not from whatever-soft. No good idea either.
Then weighing this "coming-close-to-but-surely-would-seem-to-be" beneficial software against the risk using this is a clear and very fast conclusin for me. Don't even come near to it !!
Save | Cancel
Ummm,what would I use this for? Can I use this to code emails in HTML in a way that spambots can't harvest the email addresses? Have been using a script for this purpose up til now.
Surely there is some broader consumer use for this though, right?
Save | Cancel
Hmmm,
And there are people who payed for this ?
And they gave 50 boxes for it ?
Am I alive ...
Thumbs down !
Save | Cancel
This program makes it look like someone is trying to sell their homework for a living.
What does this program do that most CS students shouldn't be able to program in their sleep by the end of their first year?
$50.. really? Sheesh.
Save | Cancel
I shall pass on this one as I think it's too much of a risk to try it. ANY program which uses code injection is a non starter for me - I don't care even if it's extremely unlikely to be a real threat (as in this case I believe) - it's a bad technique and a very clear danger sign.
Save | Cancel
Maybe this will be useful to any discussion of "code injection"...
This is from the readme file that comes with InjectedDLL.exe - one of many useful utilities available at nirsoft.com :
"DLL injection is a quite common technique used by many programs and utilities, so the fact that you have injected DLLs in your system doesn't mean that something is wrong."
Or from the wikipedia site mentioned by Funkster [http://en.wikipedia.org/wiki/Code_injection]:
"Code injection may be used with relatively good intention in some cases."
----------
Most anything, in fact programming itself can be used for good or bad. Are you going to stop driving because some people are killed or injured by cars? Still, if you want to pull up a soapbox and go all alarmist I don't think anyone is going to stop you.
At any rate, you can check the quotes provided for yourself if in doubt. Myself, I've used software from nirsoft for years, and both trust and admire the skills of the programmer (in the 1st quote) - actually a bit more so than a nameless entity called: "User:Firealwaysworks" as cited by Wikipedia. As far as HotHotSoftware.com goes, in my opinion it would be insanely stupid 1) for the author to jeopardize everything by offering malware this way, & 2) if the intent was to produce malware, there is little purpose in taking the time to write several programs, and I don't know of it ever being done -- one good malware app is more than sufficient.
Save | Cancel
I will look forward to the >Ultimate Unit Converter< from the same company (#8), it is way better than Google's converter. A lot of morons have told they could write a program like today's Text Converter. Okay, but they didn't, did they, and today's converter is both competent and free. However, I agree that the listed normal price is way too high. And whats more: GIVEAWAYoftheday is not the right place to ask how to make money (#41), is it.
Save | Cancel
To those who have no idea what this is used for and/or haven't tried it, and are either commenting or "voting": WHY? uninformed opinions from non-users are useless to others; only feedback relative to the software's functions serve any real purpose.
If something simply doesn't suit you, come back tomorrow. Maybe you'll get lucky and they'll have that "My Little Pony" screensaver you've been wanting.
GAOTD is not like a free buffet where there is something for everyone all the time, every single day. It is like a multi course meal, where some courses hit your mark and some hit others' marks.
Many of the inane comments here are about as pointless as someone's great grandmother rating a first person shooter.
Save | Cancel
#43 JM:
Where's the link???????
We're all ready here, the 500-word essay is finished and we've even done a three-word summary about The Theory of Relativity.
Hurry up.
Save | Cancel
Hehehehehehehe.....JM, I am still laughing about your comment, considering I actually own a "set it and forget it rotissere" that I bought at a garage sale for the whopping price of 5 bucks...complete with everything...it actually works well though.
As for today's program, I am going to download it anyway and see what it does.
So far, I don't think my brain needs the upgrade though, so I'll have to pass on your fantastic offer...LOL
Save | Cancel
What are hex and binaries?
Save | Cancel
You have been able to do this for decades with the Unix command "dd".
Just download the Cygnus suite if you don't want to use Linux.
DUH!
Save | Cancel
@ady state #17
I was a bit worried about your comment finding a code injection, while the others discussed encoding & encryption semantics(who cares, just don't use this for encryption, it will be unreadable but also almost unprotected)
Did you perhaps try to install the trial-download from Hothotsoftware in stead of the software from this site?
After installing the software from this site I thought the GUI being so simple that I wanted it to compare with the software on hothotsoftware. Perhaps the software here offered was an older version. But no that is not the case. But I did see a quite different behaviour though.
The GAotD could not be started as trailware but MUST be registered with the code provided (# 8 did see that to).
The trialware from Hothotsoftware could be started as a trial (but of course not registered with the code provided by GAotD).
When closing the trial a unclosable pop-up comes up asking for your email address. It wil not go away, only with CTRL-ALT-DEL as previously stated (me at #14). Wel there is another way, doing what is asked and give in an email address (this i did not choose to do).
After reading about the code injection I tried to reproduce this because this makes me very much worrying !!!
This time I did go into the second closure procedure giving some fake email-adress, and yes the pop-up closes and emedially my virusscanner warnes me about the code injection.
OK, this did not happen in the GAotD here offered. But I don't like software were the maker (#41 John) forces users to give away there data (ie email adress) without the possibility to escape. It's even worse when the maker deliberatly uses code-injection for his puposes.
Code Injection is not a normal way of behavour in good software and mostly connected to malware (that's the reason my virusscanner warned me and "ady state #17". Ofcourse you can debate that. It will be a discussion about a knife being a bad thing because you can cause harm with it or it's good because you can do nice things with it. Lets just say: In software I don't like it, though it's not always bad !!
What can make me sure that in this GAotD there are no deliberate exploits, like possible code injections once the thing is installed.
The maker showed already he makes use of this technique.
I tried some other Hothotsoftware, all had the annoying end pop-up with the code injection in the trials.
This software is not a great little nothing it's a thread to my computer security. The only thing it will do for me is giving my shredder something to do.
See: http://en.wikipedia.org/wiki/Code_injection
Save | Cancel
What to say? I am not a big programmer but I have basic knowledge. I could program such a tool within 6 hours. I would be truely ashamed to ask for money for such a thing. Sorry!
Save | Cancel
I, for one, would like an all-in-one UNIT converter. Google is nice for a single conversion, but not for multiples. This text converter I can't use, but I won't give it a thumbs down.
Save | Cancel
Well, to be perfectly honest, I have no idea what use I might have for Text Conversion Software PRO - maybe I’ll use some binary text in a graphic, & actually have it say something? The program itself is quite small, less than a meg, so it fits nicely in the equivalent of a junk drawer on my hard drive - yeah, I’m one of those people whose home has junk drawers, & boxes, & totes & , , , ;?P
I’ve found that when I go looking for a software tool, it takes a while to sort thru the choices I find with Google - sometimes quite a while - & I have to worry about malware & adware & so on. So when I need something I first go thru the junk drawer, & very often something will come in handy. I have no doubt that there are better alternatives to some of the software I’ve collected this way, but, just like in the real world, it’s something I’ve got on-hand & I didn’t have to spend a lot of time finding it. I’ll keep clutter down by not having a short cut in the start menu, or an entry in add/remove programs.
Of course some folks will probably say: “Why bother”? Well I assume that GOTD can exist because they get a lot of hits, have a lot of folks downloading what they offer, and have a lot of people clicking thru to the web site for whatever software’s offered that day. Now I don’t expect that they’ll ever offer up the latest version of Photoshop, but I do expect that the more successful GOTD is, the better the software they offer will be. Even on days when I have absolutely no conceivable use for whatever software, I still visit the company’s site to take a quick look see, feeling that’s doing my own incredibly small part to keep GOTD alive and kicking. [And no, I have no connections or anything to anybody - I just appreciate what they offer & would miss it if it went away.]
Save | Cancel
way way way to many ppl are giving this thumbs down!!! i'm willing to bet that not even half of those ppl downloaded the software before rating!!!! just becuase you dont need it dosent mean it deserves a thumbs down... and howcome everyone always complaning on how much it usually costs!?!?!?!!?!?!?! you dont have to worry about that!!! it free today from gaotd!!!!!! i personaly love the variety of software gaotd offers! i dont need everything they offer becuase my computer needs are different than other ppl's some ppl might be very thankful for this software and not care much for say a dvd to ipod convertor.... but they dont diss it! only software that isnt leisure gets all these thumbs down and bat comments. so if your gonna coment talk about the software... which by the way is cool today =) i think i will try it for encryting some documents thanks gaotd for diversisty!
Save | Cancel
Wonderful utility.
Save | Cancel
#23 Ken Kelly
Please learn the difference between encoding and encryption before YOU spout off! http://www.di-mgt.com.au/encode_encrypt.html
At very best, you could describe this program's "encryption" capability as polyalphabetical substitution, always using the same known key... the kind of thing they cracked at Bletchley House whilst killing time sitting on the toilet. :)
Save | Cancel
Don't download "Z Brain Upgrade" just yet. I have a product of my own. It's a very sophisticated, complex and intricate piece of software, entitled - "Z Brain Is A Terrible Thing To Waste."
Send $19.95 to Ron Popeil (he's my partner in development) and heck, will even throw in the Pocket Fisherman AND a $.46 discount coupon (to be used on our future products). That's a $75 value! But it doesn't stop there. If you send in your payment within the next 2 seconds and promise to tell a friend, we'll ALSO add the "set-it and forget it" rotisserie. Hurry while supplies last. Shipping is free if you pay the nominal $560 "courtesy customs surcharge."
You get it all! The "Z Brain Is A Terrible Thing To Waste" software, the Pocket Fisherman, the $.46 discount coupon (valued at $75) AND... the "set-it and forget it" thingie all for the low, low price of $19.95 with FREE SHIPPING -- IF...you pay the $560 "courtesy customs surcharge."
Please note: in-order o get the "set-it and forget it" thingie, you MUST send payment within 2 seconds AND you MUST promise to tell a friend. Simply have your friend submit a 500 word essay on the meaning of life, along with his/her gold card and expiration date and CCV or CVV2 (aka 3-digit Credit Card Security code on the back of the victim's, er, his/her gold card)
The clock startssssssss.... NOW!!!
Save | Cancel
#29. Please read the wikipedia article you linked to. The first sentence states:
"In cryptography, encryption is the process of transforming information (referred to as plaintext) using an algorithm (called cipher) to make it unreadable to anyone except those possessing special knowledge, usually referred to as a key."
From this description, the KNOWLEDGE of the algorithm is sufficient to constitute a "key". Yes, calling this encryption in today's high-security environment is a little dodgy, but still technically accurate. Yes, obfuscation would probably be a better term to use, but by the strictest definition of the term encryption, this would qualify.
If you look at the history of cryptography, one of the earliest ciphers (used in the Roman Empire) was a simple letter substitution (similar to the cryptograms you see in the daily paper or the magic decoder rings that come in kid's cereal boxes). ROT13 also falls under this type of "encryption". The key for these consisted of a table matching the original letters to the ciphertext letters. ROT13's is a simple shift and this one would be the ASCII/hex/octal table. The problem with all of these type of letter substitution ciphers is that they are subject to statistical analysis with a little knowledge about the language used and method of encryption used. This method has the same weakness.
So, is it encryption? In the strictest sense of the definition, yes.
Is it STRONG encryption? NO.
Save | Cancel
I agree with number 6 to a degree. I dont think everone should download a game but maybe they should just for fun. Im going to wait till tomorrow and check it out.
Save | Cancel
download and installed just fine, think price is to high. thanks
Save | Cancel
This must be a joke. I received an error message while installing on XP SP2. However when I abort the install, my browser goes to GOTD's "successfully installed and registered, now what" page. I think I am going to run a virus scan just to be safe.
Save | Cancel
As a programmer and a forensics expert, I see no need for this program--and I am VERY suspicious of anyone who sells software and claims it "encrypts" without understanding what encryption is and means.
Even running material through multiple, real encryption algorithms usually does not improve, but reduces security.
What intrigues me is how many software writers seem to be unable to bother to take the time to explore what already exists, but instead spend their time creating less useful versions of what already has been created.
Such an exercise is very useful for the programmer to help them understand how to do certain things, but it is unlikely to result in a useful or valuable product without spending nearly as much time as those who already have created a program for that use.
The first rule of engineering, be it physical or logical, is to research what has been done by others--avoid re-inventing the wheel!
If you have researched, AND you have found only programs which do not have functions and abilities which you feel are needed, AND the programmer who wrote it doesn't feel that they are needed, or cannot for some reason spare the resources to add those functions, AND you have the time to spend writing a version which does exactly what YOU want it to do, THEN is the time to write your own program.
But it is not a "product" unless there are others who desire or need the functions you provide. Nor is it a "product" if it doesn't work reliably.
This problem of not understanding the difference between "it works!" and "it's finished!" is common with new artists in any field, although it is most common in programming among managers, who feel that if the core works, the program is done, when in fact, until the program's interface is functional and all error-trapping routines are finished, the program is only "90%" done, and it has proven over time that that last 10% will take as much effort as the first 90%.
I learned decades ago to write the user interface first, write and implement the core code, but never, never show management a version which performs all needed functions, but which is not finished inside where it deals with errors and exceptions. This way management is much less likely to declare a program "done" when it is still in dire need of work.
Another useful thing to remember is that "temporary" tools require the same attention to detail that any "permanent" tool requires. Such programs have a way of being useful far beyond your initial purpose.
(I did system conversions for many years, and wrote many temporary programs. Even the programs which never got used past the conversion were used so often during the conversion that it was worth the extra time to make them as bomb-proof and easy to use as any other program.)
One of the things learned about software over the past 60 years is that programs have much longer lifespans than we ever thought they would--the IRS was still using code written in the early '50's for IBM calculators which were long obsolete, well into the 1970's, running them on other machines in emulation. There are still companies whose core business is dependent upon COBAL code which dates from the mid 1960's.
Save | Cancel
I don't see how anyone would buy this. I can already do any of these conversions online and for free.
Save | Cancel
I did not even need to launch Returnil's VPC this morning but, as a precaution it is running for GOTD downloads. #19; NO, there is no guarantee posted anywhere on this site. All software is presented "as is" with no warranty expressed or implied. GOTD is quite right not to offer such a legal entanglement. #7; I wonder how many people got the binary to text "word problem" aspect of the joke, LOL! For simple encryption try TrueCrypt (desktop) and its companion AxCrypt (embedded).
Save | Cancel
Too many posters are getting all antsy about the claim that today's offering has an encryption function.
Those posters don't think so.
Instead of coming on here to moan, why didn't they first make use of this same developer's Z Brain Upgrade software?
This would undoubtedly have upgraded their thought processes to such extent that they would now believe that:
(a) Text Conversion Software PRO does indeed encrypt, and:
(b) the Moon is made of green cheese.
Thanks, GOTD, for allowing my attention to be brought to the existence of both apps.
I'm off now to make lunch for the fairies at the bottom of my garden.
Save | Cancel
Mine is encrypted Ken
Save | Cancel
Ken kelly,
Must you put na in the space for a website address. Do you not know what that space is for.
It is to link to the website you dont have??????????
Save | Cancel
Yo #25,
After taking a quick look at hothotsoftware.com, it appears that a few of their programs might actually be useful. But they also have a lot of questionable offerings like today's giveaway.
Surely, after reading #11 by Flattop, you understand that (in the same spirit as the "Brain Upgrade") #8 is not to be taken seriously.
I have to agree that today continues the recent trend of giveaways that aren't worth the bandwidth to download but still I'm entertained by reading the experiences of those who voluntarily put their computer systems at risk with a lot of these programs. Overall, I believe that we take these freebies too seriously and would all do well to patiently await the occasional gem from this site and just blow off the rest.
Save | Cancel
@23 Sorry Ken but that is NOT encryption, it is obfuscation. There is a difference, I hope you don't actually think that simply changing the format is encryption, even if you do it multiple times. You may want to read up a little on security before you think others are spouting off on topics you know little about. This app DOES NOT perform any encryption what-so-ever.
Save | Cancel
To Ken Kelly as well as HotHotsoftware
http://en.wikipedia.org/wiki/Encryption
Learn what a word means and how to use it properly before making any claims.
John McPhearson & TK where utterly correct to find the "encryption" claim to be ridiculous.
As for the rest of the program let it suffice to say that it only has a very limited user group of which most of them would easily be able to code something themselves that serves the purpose. Those that would be unable as of yet will easily find free converters averywhere. This is once again a program by someone that thinks that because they made it it must be worth lots of money.
ROFL
Save | Cancel
I wonder if one could do a digging into closed source program code?It is not hex or binary?
Well not that I have time to be a script kiddie and no schooling for real hacking.So friggin idea what to dig for in closed source progs?
Not many comments as yet,yes few mentions what is useful for.Maybe later on someone may come up with an interesting idea.
Save | Cancel
well... none of you ARE paying for it... so what is the point of bitching?
what does the purchase price have to do with anything involved here?
plus, they, or anyone selling anything, can charge any price they wish... and people can choose to purchase anything at whatever price they feel is acceptable...
Save | Cancel
#16, No1, assuming the brain upgrade was an April Fool's joke, I started to place an order and it did add it to the shopping cart. Draw your own conclusion.
Save | Cancel
To #8 you can pass on unit conversion...Google do that for free without any installation !
Save | Cancel