Every day we offer FREE licensed software you’d have to buy otherwise.

Giveaway of the day — Erelive Data Recovery 6.6.0 for Windows
Erelive Data Recovery 6.6.0 for Windows was available as a giveaway on November 29, 2020!
Erelive Data Recovery can recover lost or deleted photos, music, video, document, archive etc from Windows or laptops Hard Drives including recyle bin, external hard disk, flash drives, memory cards,cameras and camcorders etc.
It can recover deleted files from all kinds of media storage devices, including recover lost date from Windows computer or tablets hard drive, SSD, USB drive, camera or camcorder memory, SD card, MP3 player, MP4 player, game box etc.
Supported files types:
- Recover Photos and Images like JPG, TIFF/TIF, PNG, BMP, GIF, PSD, CRW, CR2, NEF, ORF, RAF, SR2, MRW, DCR , WMF, DNG, ERF, RAW, etc.
- Restore Audio, Music format like M4A, MP3, WAV, WMA, FLAC, AIFF, DTS, MID, MIDI, OGG, AAC, QCP, AMR, etc.
- Relive Videos, Movies like AVI, MOV, MP4, M4V, MKV, AVCHD, MTS, M2TS, MXF, XAVC, H.265, 3GP, 3G2, WMV, ASF, FLV, SWF, MPG, RM/RMVB, etc.
- Retrieve Documents like Word DOC/DOCX, Excel XLS/XLSX, PowerPoint PPT etc
- Recover Archives like RAR, ZIP, BZip2, 7z, SIT, SITX, SYS, LIB, DLL, 7ZIP, GZIP etc
- Recover other lost files like Email content, EML, PST, EMLX, MSG, DBX, EDB, BMS, NSF, BKL, BKS, PAB
System Requirements:
Windows XP/ Vista/ 7/ 8/ 10
Publisher:
EreliveHomepage:
https://www.erelive.com/data-recovery/File Size:
11.2 MB
Licence details:
Lifetime, no updates
Price:
$49.99
Featured titles by Erelive
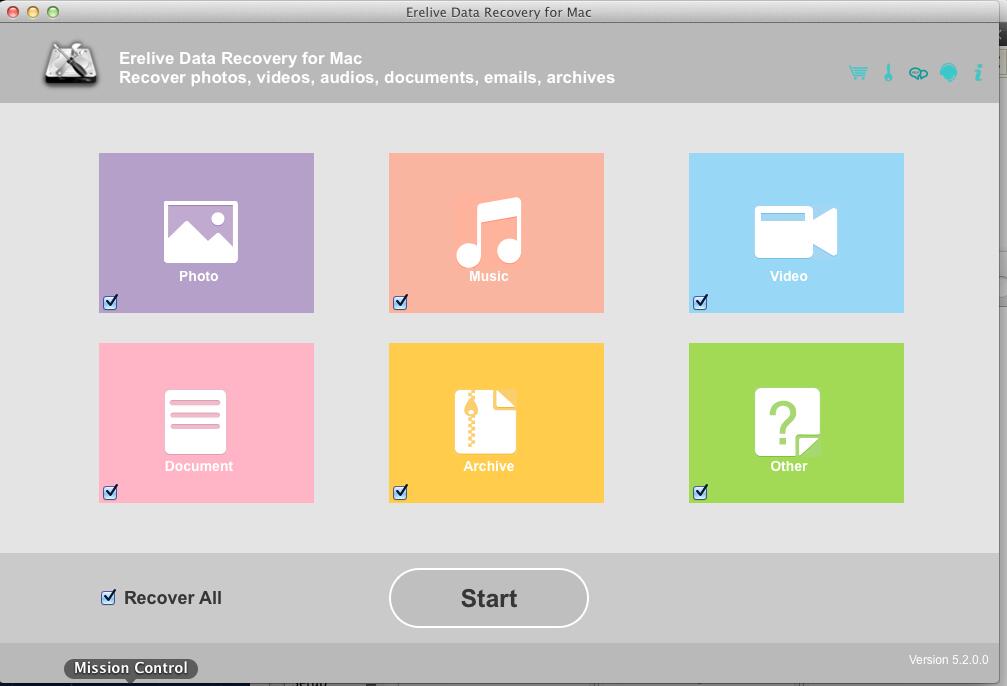
70% off discount coupon code: 70%OffDiscount The lifetime update license can work on two computers. Support free lifetime update and support. Erelive Data Recovery can recover lost or deleted photos, music, video, document, archive etc from Windows or laptops Hard Drives including recyle bin, external hard disk, flash drives, memory cards,cameras and camcorders etc.
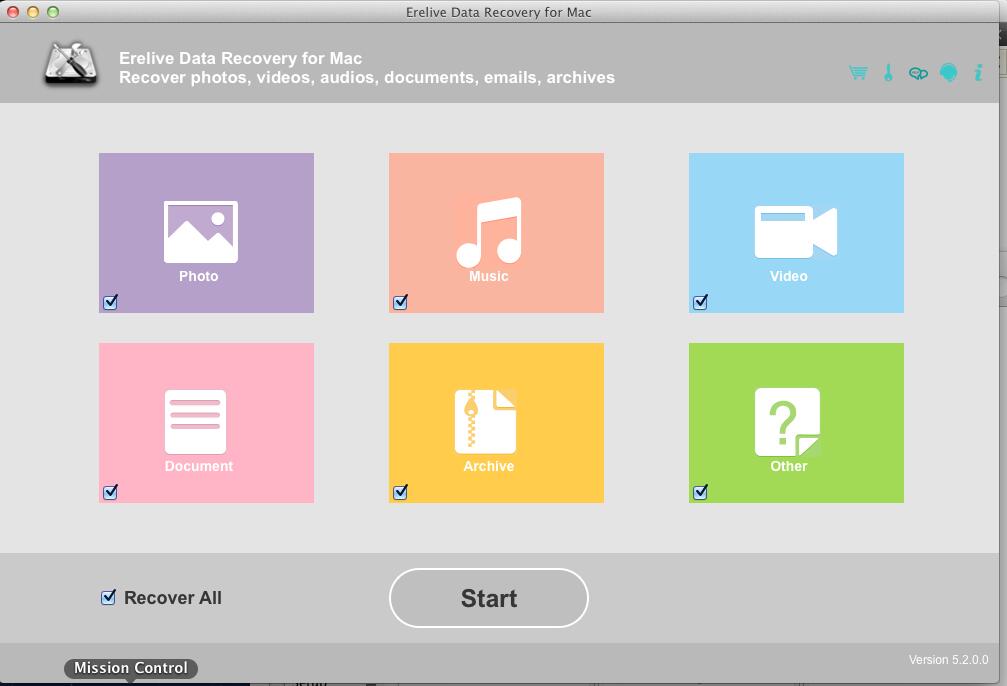
70% off discount coupon code: 70%OffDiscount The lifetime update license can work on two computers. Support free lifetime update and support. There Is No Limitation in Lost File Size! Recover and Relive Lost files, Accidently Deleted Data, Permanently Deleted Files from macOS, Mac OS X, Time Machine Backup Drive, External Hard Drive, Flash Drives, Memory Cards, Cameras and camcorders etc.
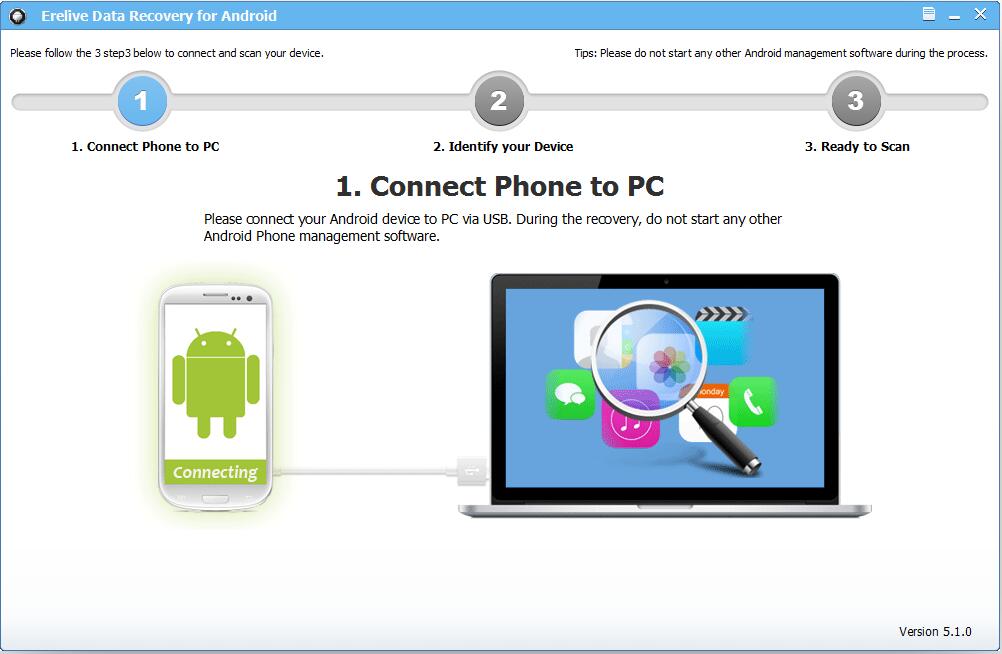
70% off discount coupon code: 70%OffDiscount Recover Android phone or tablets lost contacts, messages, call history, photos, videos, music files, documents, and more from Samsung Galaxy, Google Pixel, HTC, LG, Android One Moto X, Sony Xperia, Nvidia Shield Tablet, Samsung Galaxy Tab, Sony Eperia Tablet, Xiaomi, Huawei etc.
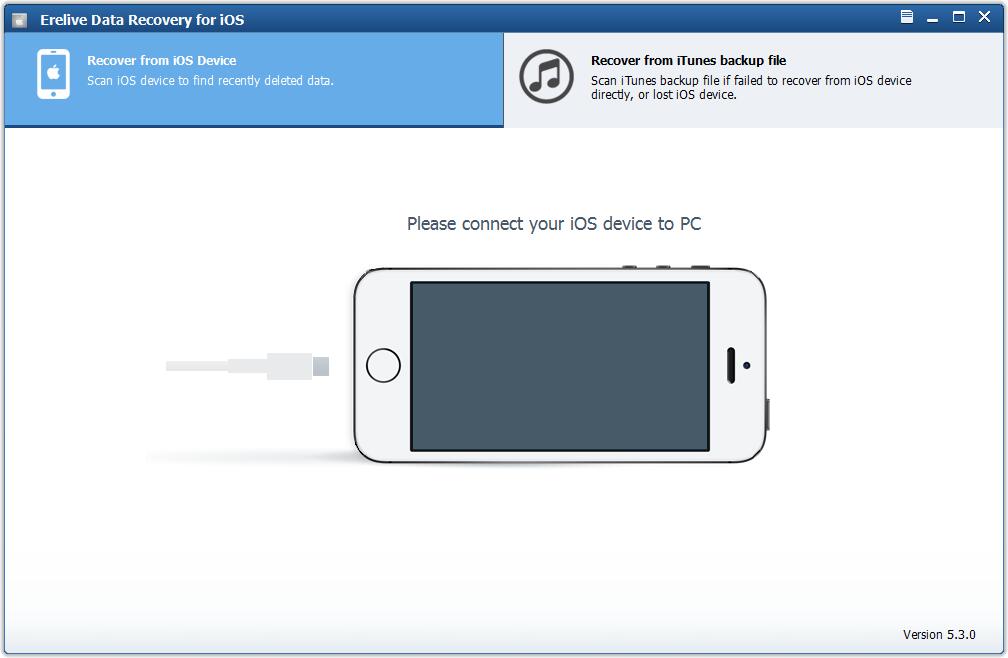
70% off discount coupon code: 70%OffDiscount Recover Photos, Contacts, Message, Voice Menos etc from iOS Device including iPhone, iPod, iPad. For Example, Recover iPhone Lost Data Due to Screen Deletion, iOS Upgrade/Downgrade, Factory Reset, Jailbreak, Water Damage, Screen Broken, Stuck in Apple Logo, Stuck in Recovery Mode, iPhone Lost/Stolen, iPhone Locked etc.
GIVEAWAY download basket
Comments on Erelive Data Recovery 6.6.0 for Windows
Please add a comment explaining the reason behind your vote.


I downloaded this file. (attempted to) My MS security would not allow it to be load (opened) unless it is over ridden by operator. I clicked on more information and it told me that the creator was not disclosed and that there was no certificates. I elected not to down load it, based on this warning form my MS - which is not may security program - that runs constantly. It does not act until the file is actually downloaded or possibly even until actually installed.
Any program from an unknown source with no certificate (not even an expired one) should be downloaded and activated without much serious thought and research of it's source and history.
Save | Cancel
I have bought the 1 year license before and it did a great job to recover my lost photos and other files.
I have not met any safety issue during or after I used it.
Now I will buy the lifetime license with the 70% off discount. It is the biggest discount I could find. It is even cheaper than the 1 year license.
Save | Cancel
Use Recuva - its much better !!!
Save | Cancel
I've never had Windows 6.6.0 & why would I want to recover it if I did?
(That's a joke "Son" )
Save | Cancel
EULA does not exists in China nor it is allowed to be used. Any vendor from China has integral rights to ravage your computer data at will, unknown to the user and in background, it is normal behavior to them. All, I repeat, All software in China is controlled by the government, be careful.
Save | Cancel
kerry, It is totally wrong. If it is controlled by the government, why products from China are popular all of the world.
Save | Cancel
kerry, Please provide the evidence that it can ravage your computer data, please firstly prove it before saying it.
Save | Cancel
kerry, This is the reason I don't download any chinese softwares. This is the reason the Indian government has banned more than 150 chinese apps and games.
Save | Cancel
kerry, You know this how exactly? Sounds like propaganda.
This said, unless someone can show me a link between proxydoctor.com and the military industrial complex or US or British intelligence, I think that based on the information there, I have to pass.
Save | Cancel
Thanks to everyone on this thread for your detective work. I won't be downloading this one.
Save | Cancel
Ava, Ava, It is safe to use. Those who said it is not safe, there is no evidence to prove it, it is hostile attack.
Save | Cancel
krypteller, Great recommendation. I have used Recuva before. Thank you.
Save | Cancel
Helen, That makes me feel so much better. Still not downloading it.
Save | Cancel
Thanks TK for the IP. Here is where it traces to:
inetnum: 123.112.0.0 - 123.127.255.255
netname: UNICOM-BJ
descr: China Unicom Beijing province network
descr: China Unicom
country: CN
Sorry, I won't install an app that hides their Chinese company info.
On their website, the lines at the bottom of the page should link to some statements about copyright or privacy. There is no links... not good!
Copyright 2020 Erelive All Rights Reserved Privacy
Save | Cancel
It would be helpful if you let us know where these software companies are located. Are they located in Russia, China, etc?
Save | Cancel
TK, smells like xenophobia.
Save | Cancel
It is only possible to recover from the hard drive, files that were deleted 3 years ago - if you do not use the PC for the past 3 years since deletion of those files.
Otherwise, the hard drive sectors would be over-written. It would not be possible to recover the files in that case.
Being a shill requires expertise. Otherwise it is easily exposed.
Save | Cancel
ricohflex, I think it can be recovered
Save | Cancel
Rajesh Pabari, it is not correct, the files that were deleted 4 year also can be recovered, just times it
Save | Cancel
Gold nuggets for sale in +27719992769
We are the leading sellers of the following mineral Gold bars and Gold Nuggets 99.67% purity 24 carats of Congo origin (DRC) South Africa (Gold Nuggets).on good price. We can supply Gold up to 100 kilograms or even More at a generally low price to meet the buyers resell value for his money, Buyer is free to come down for inspection and viewing of the goods. Kindly contact us if you are interested,
Save | Cancel
Thank you for sharing this giveaway, just test it and it helps to recovered my deleted music, video and word files 3 years ago, it is really powerful.
Save | Cancel