Every day we offer FREE licensed software you’d have to buy otherwise.

Giveaway of the day — PowerCryptor 1.01.04
PowerCryptor 1.01.04 was available as a giveaway on April 14, 2014!
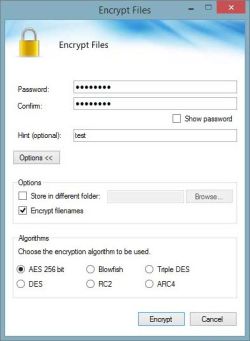
PowerCryptor is advanced and easy to use encryption software. It password protects your highly sensitive documents, photos, music, videos and other files. PowerCryptor has a modern easy-to-use interface, and supports the most secure encryption algorithms, including AES 256-bit.
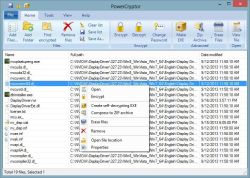
Encryption with PowerCryptor is easy to do and completely transparent. To password protect your file or folder, just right-click on it in windows explorer and choose Encrypt. PowerCryptor makes it as easy to open, edit and save encrypted files, as it is to work with unencrypted files. PowerCryptor also allows you to encrypt filenames. You can create self-decrypting .exe file to send password protected files via e-mail. PowerCryptor includes advanced password generator that creates really strong passwords. With PowerCryptor you can securely erase your files and folders beyond recovery. This way, your privacy protection is ensured and no one will be able to access your confidential data.
System Requirements:
Windows XP, Vista, 7, 8, 8.1 (x32/x64), Server 2003, Server 2008, Server 2012
Publisher:
KRyLack SoftwareHomepage:
http://www.powercryptor.com/File Size:
11.5 MB
Price:
$29.95
Comments on PowerCryptor 1.01.04
Please add a comment explaining the reason behind your vote.


I like this giveaway, but it would have been much better if their were a self extracting feature incorporated within the program.
Thank you.
Save | Cancel
Creating a backup to anything you will be encrypting, prior to encrypting, is the easiest way to skirt one of the concerns that relates to the aftermath of a system crash and potential permanent loss of files.
The fundamental of keeping a document secret is not to have un-encrypted copies of the same thing lying around. It defeats the purpose of encryption.
Sort of like (but not exactly) keeping $10 Million in a safe with a powerful combination lock at home. But at the same time, in case you forgot the number key combination to open the safe, you have another $10 million in cash in a plastic bag lying on the sofa at home.
Save | Cancel
#32
"A volume could have only one file in it. You can create as many volumes as you wish if you want to have all your files separately encrypted."
In #16, I mentioned that Truecrypt is not really suitable for encrypting single files or a folder of files. This is because it is not designed for this purpose. You can certainly use it to encrypt single files if you don't mind the hassle (which is considerable) of creating a separate volume each time you wish to encrypt a file. This is almost like using a sledgehammer to crack a nut.
Save | Cancel
#29- this giveaway appears to be the pro version- the free version does not offer any choice of encryption methods, nor the ability to make .exe files or zip files, not to erase files. On the other hand the free version enables you to save the installation file so that it can be reinstalled if the programme is lost.
Save | Cancel
#4
#7
I personally use the Time-Freeze feature offered in the ToolWiz Care bundle, but I believe it can also be downloaded as a stand-alone tool.
It is absolutely capable of handling the demands of a casual/amateur user.
Karl also linked a very nice advanced system virtualization software. It can handle anything related to a system virtualization tool.
ToolWiz Care's Time-Freeze is very simple, requiring just a couple of clicks to activate it and a simple restart to revert your system to it's state prior to engaging ToolWiz Care's Time-Freeze
_________
As-far-as today's offer, it is hindered by some legitimate concerns, but they are minor - unless the user is unaware of the concerns.
I'd recommend doing a little research to reveal the concerns surrounding this software.
Creating a backup to anything you will be encrypting, prior to encrypting, is the easiest way to skirt one of the concerns that relates to the aftermath of a system crash and potential permanent loss of files.
Save | Cancel
#14: "Every day some of the posts here are from people concerned about losing their hard drives and all their GOTD installed programs. Instead of living in fear they should periodically clone their hard drive. Then in the event of catastrophe they can install the cloned drive and start from exactly the point when the drive was cloned. It’s Computing 101 amd should be taught in schools."
It works, but it requires a 2nd hard drive. That makes it wasteful, expensive, & impractical
I just bought WD Black drive because while more expensive, even on sale, it has a much lower failure rate than cheaper alternatives, where that rate appeared to approach 30-40%. Overall it seems the current drives on the market can only be considered reliable if they make it past the 1st several months in operation. So for the purpose of protecting your stuff you'd want to run the drive for say, 6 months, then use it for your stored clone if it survived that long.
The Paragon backups I make take roughly the same amount of time to create -- raw data's copied either way -- but the archives take up less space & are effectively *a clone in waiting* of your hard drive(s) or partition(s). I can restore them whenever I want to a real or virtual drive -- I can store them on hard drives or optical discs or USB sticks. The only area I can think of where an actual clone might be better is file copy transfer speeds -- I can stick a hard drive in my USB 3 dock & copy files faster than from a mounted Paragon backup archive, because of the overhead involved in mounting the archive to read & copy individual files/folders.
Where clones do work well as immediately available backups is when you're using something like a VM server -- you have the server simply load another VM. Want the server to run a different OS, load another VM instead of the currently loaded VM. If a copy of the OS becomes damaged or infected, load a duplicate copy. Want to restore an OS - load a copy made before whatever changes were made. Hard drive goes bad - load a copy stored on another drive.
This sort of thing can also work well for loading PCs BTW -- restored a backup of a win7 HP 64 VM to a hard drive, stuck it in my son's new PC, used Paragon's P2P software, & 6 minutes later the PC was running a fully up to date copy of win7 SP1, complete with generic stuff like web browsers, Adobe's Acrobat Reader, 7-Zip & so on.
While it won't work with some apps that use your hardware ID for registration [though keeping the same hard drive serial helps - use Sysinternal's VolumeId], it's certainly possible to keep a VM up to date including all your preferred software. Then you can transfer that VM's disk to a hard drive or even a VHD [bootable in win7 onward], adapting it the same way to most any hardware capable of running that OS.
Save | Cancel
KZ #23 Just Google Clone and there is pleura of options out there. System Image is the same thing really and if you are not doing some kind of serious Back Ups it will bite you, not if but when.
I use Macrium Reflect and do a daily System Image (Clone). Excessive yes, but guess what it saved me tons of turmoil last week when my 2TB HDD crashed and burned! Picked up up a new HDD and was back in business in a couple of hours without loosing a thing!
I chose to purchase the product for my daily backups, yes I do that also as a fail safe. Oh, and did I tell you I also back up to the cloud once a week. Yeah, I do that also, never to save when it comes to our data.
As far as this product I choose to pass on it as I also use 7Zip.
Save | Cancel
If you need a real good encrypter use truecrypt ! It's free !
Save | Cancel
Purely speculation on my part, IF as alleged the NSA [& I assume other intelligence gathering agencies] took an active role in developing software & standards, then private, & perhaps less popular software in general, might have escaped such "interference".
Aaron Farnsworth mentioned that the Brazilian gov & the FBI were unable to crack Truecrypt drives. Recently the US gov took down the Silk Rd, a on-line marketplace of illegal goods & services located in the darknet. The basis for the darknet, & TOR & onion, originated with the gov, & it's been rumored for quite some time that the gov could get around its privacy protections. It's also been rumored that they wanted to keep those capabilities secret -- until they took down the Silk Rd., they were. Before & after they took Silk Rd. down a lot of illegal activity took [takes] place using the darknet -- something obviously changed for them to go after Silk Rd. but whatever it was they haven't closed down the Silk Rd.'s competition. Again this is pure speculation, but if the US gov [the NSA etc.] let illegal activities go on rather than compromise the gov presence & capabilities, the same way the CIA is said to have tolerated all sorts of illegal activities in the past, then the gov's supposed inability to master Truecrypt **may** have been just a matter of restraint... maybe it was a choice of helping out a criminal investigation in a country often considered only somewhat friendly to the US, vs. protecting a valuable secret capability?
I'm just cynical, & don't like to take what any gov says at face value, particularly when it's reported in the media. Make up your own mind. FWIW KRyLack Software, Kiev, Ukraine, 03127, Serhiy Horobets. http://krylack-software.software.informer.com/
Save | Cancel
@KZ. Perhaps, I can answer your question. You can clone your harddrive to eksternal harddisc with the freeware program : Aomei Backupper. You can even burn a Windows PE disc with it. Greets from Denmark.
http://www.backup-utility.com/free-backup-software.html#
Save | Cancel
#4 - Shadow Defender is what you want - best one of it's type out there. Per #1 I won't even bother installing this one as those are good reasons to skip it.
Save | Cancel
#3: "Again the usual (but important and meaningful) question.
Say for example, I use this giveaway encryption software to encrypt hundreds of important documents.
Then my PC crashed due to malware and this giveaway software was damaged by the crash.
Due to the 1 day expiry limit, this GOTD software cannot be re-installed.
Say good bye to the hundreds of important documents.
Oh, wait. There is a way. Quickly shell out US$30 to buy the software. If the software company has closed and is no longer in business (like so many others)and you cannot even buy it online or at the software retail store, then you are in trouble."
.
If you're talking about encrypting a high volume of data or files you probably want to go with something like Truecrypt or have the encryption in your database software etc., the point being you don't want to be hassling with manually encrypting all those individual files or folders -- with Truecrypt for example everything stored on the [virtual] drive would be encrypted, so all you have to do is save your files/folders there.
If you're talking about long term storage decide what are your security requirements & work backwards from there. If you don't need fairly instant access to stuff that's not current, then why keep it on hard drives, where you'd have to maintain mirrored storage of some sort, maintaining [replacing] drives as necessary over years. And if it's not on storage connected to your system(s) & network, e.g. you've got the data transferred to optical discs, do you need that data to be encrypted? A hacker or cyber thief isn't likely going to come to your home or biz & crack your safe. Something else to bear in mind... not every program that worked on win98 worked on XP -- not every app that worked on XP works on 7 -- not every app that works on 7 works on 8.1. Are you willing to keep old versions of Windows running just so you have access to old encrypted data? If not, & assuming you decide you need that data encrypted, then you should probably stick with something like password protected zip files, which are more likely to be usable for years & years.
To your original scenario... If/when a drive dies you've lost whatever was on that drive -- that's why if data's critical it should be stored on more than one drive. You should have a full disc/partition image backup -- the software's free, & if you can't afford external dives for backup storage, DVD burners can be had for $14, & 100 DVDs for < $20. Then you restore your backup to another drive, your encryption software's still there & working, & a copy of your encrypted data is available wherever you stored it. If everything was on the [now dead] drive, & you don't have a backup, you don't have the data you'd need to decrypt anyway. If your data's been copied to another drive, & you've been too lazy to perform a hard drive backup, then yes, you'd have to hope a trial copy of the encryption software worked to decrypt your data, or pay for the full version, or store the encrypted data as self extracting [.exe] files, or use a free-ware or open source app for the encryption to start with. But then again, if you're that forward thinking that you recognize that possibility, you would not go without a backup, would you? :)
RE: mal-ware, it generally steals data, &/or deletes it, or holds it hostage. Unless it's sole purpose is to trash systems it's not likely to cause any sort of crash that would tip you off to the fact that you might have been infected. That's not to say that you can't have a portion of your system hard drive physically go bad, which does happen with regular hard drives -- when that happens whatever was written there is often gone forever. Otherwise corrupted files normally become corrupted when there's a problem saving them to whatever storage medium, e.g. you have whatever doc open as you're working on it & you have a power failure, so the doc as it is at the time of that failure only exists in memory, which is cleared without power. Program files may be read into memory, but those files on your hard drive aren't re-written or saved, so what was there before a power off or crash aren't effected.
If you don't have a clean backup, & you have to reinstall Windows [because of mal-ware or any other reason], then you'll lose most of your installed GOTD offers. Such is life. In that case if you have something encrypted with an app you got from GOTD, store a decrypted copy of those files somewhere else before you reinstall Windows. Or just buy the app, which by rights you should do anyway to support the software company if you use their product regularly. That said, if you're re-installing Windows because of mal-ware, I'd suggest that there's a good chance the encryption key has already been stolen, so it might not be a bad idea to decrypt [& re-encrypt if you want] that data anyway.
Save | Cancel
#16
"Truecrypt is excellent but it is not really suitable for encrypting single files or a folder of files. It is for creating encrypted volumes (vaults) that contain files inside it. You can also create an encrypted hard disk partition. After you sign in to the volume or partition, files are automatically decrypted or encrypted on-the-fly as you use them."
--------------
When a Truecrypt "volume" (basically a Windows folder) is mounted you immediately see the file(s) in the volume. A volume could have only one file in it. You can create as many volumes as you wish if you want to have all your files separately encrypted. Or you could have the 1st volume that opens contain folders with one or as many files in them as you wish.
Truecrypt can also use a keyfile in addition to passwords. Just don't loose your keyfile.
Save | Cancel
@4,6,7,8
I've been curious about Karl's removing by reboot as well and was elated to have it addressed. I greatly appreciate the help that is offered kindly by all. Thank you Karl.
Save | Cancel
I like and use Axcrypt and Truecrypt. Both are freeware.
Save | Cancel
Looks like they also offer a free version.
Wonder what the differences are...?
"PowerCryptor Free Edition"
http://www.powercryptor.com/powercryptor-free-edition/
Save | Cancel
Been using Easy Crypto (freebee) for about 20 years now. Nothing easier to use. Just right click ,enter a psssword and enjoy. Just don't forget your password :)
Save | Cancel
@23 agree that this is necessary I have the tools thanks to a giveaway here recently but not the smarts to get it together
have passed on many GAOTD BECAUSE i DO NOT HAVE A VIRTUAL MACHINE I WOULD appreciate being directed to a free or paid tutorial re how to get this done
Save | Cancel
#8 Captain Commando
Agreed, it's always well worth mentioning 7zip on these occasions, particularly since many are not aware of its encryption abilities.
Perfect for single files or folders without need of a virtual drive.
When it comes to security, open source has to be the way to go.
Save | Cancel
FWIW, as #18 intimated, anyone using an archiving program (7zip, winrar, haozip etc.) has an equivalent (but more reliably-sourced) alternative to this. You don't really need a separate program but if you need the convenience of right-click encryption (decryption is transparent with archiving) Axcrypt is the (highly-vetted) standard unless you want to travel the TrueCrypt road.
Personally, I would *never* trust encryption to some company-less dude with only an email address who shows up at your doorstep slinging his ware because God only knows what kind of coding he has put together.
Save | Cancel
#11 ric, I understand what you mean, perhaps the activation code is only valid for 24 hours, as the installation thanks you for installing the Giveaway version of the program. What I was trying to do was see if either GOTD or the developer would reply to confirm or deny that it can be reinstalled and reactivated after the giveaway period. So far, nothing.
Save | Cancel
Carl K @ #14. So, would you be kind enough to 'skool' us after your comment. Sincere request - it would be a useful and appreciated thing to learn how. Don't leave us hangin' like that! ;) Thanks, K
Save | Cancel
#21 Brian
What would be cery helpful would be to have a seperate unencrypt program that is free.
There is a nice free solution. It's TruPax. An independent "frontend" to truecrypt, but without shared code.
http://coderslagoon.com/home.php?lang=EN
Save | Cancel
I am also concerned that if I encrypt my files and have a computer crash I won't be able to uncrypt the files as I can't reinstall tne program as its a GAOTD.
What would be cery helpful would be to have a seperate unencrypt program that is free.
Save | Cancel
Every software of this kind should be accompanied by an always free to install companion software that can only decrypt. Let's call it a reader.
Save | Cancel
I am using Zero Footprint Crypt (freeware). Is this GOTD program better in any way?
Save | Cancel
Impressive giveaway! The software itself works well and is very easy to use. File encryption, folder encryption, both were child's play for powercryptor. Even then as Karl said, the list of concerns is too long. We encrpyt data which we don't want others to see but imagine a scenario when we cannot access our own encrypted files or folders! Doesn't seem so nice now, does it?
For years now TrueCrypt has been providing free encryption. But don't be mistaken. Its not the average encryption that it provides. It provides the encryption of the highest degree. Check out this excerpt from the Wikipedia page:
In July 2008, several TrueCrypt-secured hard drives were seized from Brazilian banker Daniel Dantas, who was suspected of financial crimes. The Brazilian National Institute of Criminology (INC) tried unsuccessfully for five months to obtain access to his files on the TrueCrypt-protected disks. They enlisted the help of the FBI, who used dictionary attacks against Dantas' disks for over 12 months, but were still unable to decrypt them.
http://www.truecrypt.org/
Other honorable mentions include AxCrypt & 7ZIP [i absolutely love it].
http://www.majorgeeks.com/files/details/axcrypt.html
http://www.7-zip.org/
Have a nice day!!
Save | Cancel
I use Safe House Software Professional, this one doesn't seem to be tied a professional company or at good reputation.
Save | Cancel
@13: Truecrypt is excellent but it is not really suitable for encrypting single files or a folder of files. It is for creating encrypted volumes (vaults) that contain files inside it. You can also create an encrypted hard disk partition. After you sign in to the volume or partition, files are automatically decrypted or encrypted on-the-fly as you use them.
A freeware similar to today's offer is the excellent AxCrypt which is integrated into the Windows OS, so you can right-click a file or a group of files to bring up a menu of options. It supports the use of a password, and/or a keyfile, shred and delete, and it can create encrypted exe files that do not depend on an installed copy of Axcrypt for decryption.
I use both Truecrypt and Axcrypt extensively. They are free and excellent but they serve different encryption requirements. Highly recommended.
Save | Cancel
# 4 Bobby Joe
Toolwiz Timefreeze (FREE) is the answer to your question:
http://www.toolwiz.com/en/products/toolwiz-time-freeze
----------------------------------------------------------------------
As for today's giveaway is a good software, but for apps like this is better switch to open source products....
http://elefantsoftware-en.weebly.com/encoding-decoding.html
http://stefanstools.sourceforge.net/CryptSync.html
http://hummerstudio.com/filewall
http://www.ravib.com/cryptola
http://www.giantmatrix.com/products/aplus-folder-locker-free-edition/features
http://www.xoslab.com/efl.html
http://www.toolwiz.com/products/toolwiz-bsafe
http://www.axantum.com/axcrypt
Enjoy!! ^_^
Save | Cancel
Every day some of the posts here are from people concerned about losing their hard drives and all their GOTD installed programs. Instead of living in fear they should periodically clone their hard drive. Then in the event of catastrophe they can install the cloned drive and start from exactly the point when the drive was cloned. It's Computing 101 amd should be taught in schools.
Save | Cancel
Why not just use TrueCrypt?
truecrypt.org
its free, no registration required, works across windows and linux.
provides complete HDD encryption.
Save | Cancel
Addendum to #1
This program works with passwords. This is abaolutely sufficient in most cases. Unless you use passwords with minimum 20 mixed character from ²d€ to +Ä ...
You cannot use keyfiles with this SW.
For high security you should use keyfiles AND a password. The reason for a keyfile like :
LIB679/&F/65fwdcv/(%/FW&Z/V"!XZVXöoih0IUlhIBo87!P)//G!E"78gd2<87gvy483y7v<V(!&v3408h08H<ü0)(H<9(Hubp928ge/"$§/$§%=(ZNBJR?)U$"%BPU)g<BUG²€fÖOIjn097ZHGBo9(&GvI/fdÖoge
is, that the one, who wants to crack the message needs PHYSICAL access to the computer to access a least a possible keyfile ... and there is still the password left. A message sent over the NET is still not crackable by anybody (unless there is no backdoor in the SW itself). But the receiver needs the keyfile too.
The absolute best encryption method are OneTimePads. With the risky disadvantage of save distribution of the OTP (one time pads) and the strict use of ONE TIME. (Google!)
Save | Cancel
Ghenghis McCann #5
But will the activation key still allow you to register and use the software, even if it can be installed again in future.
If not, then it remains un-useable to decrypt your locked data.
Save | Cancel
Thank you to all those who answered my question....have a great day/night
Save | Cancel
Today's program looks like a nicely developed piece of software in the way it integrates into your system.
Having said that would I use it, NO.
If I want to keep nosy Parker's out of my business I would use something we all use everyday, a compression program but with encryption, powerful enough for most of our needs and always available.
To really hide something, it needs to be open source and powerful and that means its PGP.
Save | Cancel
@ 4 Bobby Joe
Karl used Faronics' software called DeepFreeze, no matter what changes his computer experiencing, it will be back to earlier state after a reboot.
About today Giveaway, i will skip since i have free and open source 7zip.
Save | Cancel
#4 Bobby Joe
Yes, I run my software always with a virtual layer. This is in my opinion the only way to keep a system clean and safe. You can use the free Toolwiz Timfreeze or the highly recommended paid (35$) Deepfreeze Standard.
I ONLY install and test in a virtual system.
Save | Cancel
@ 4 Bobby Joe
Download virtual box or vm player!
Get a os like
winxp (need 128mb mb ram minimum)
or latest windows7/8 (need a least 4-6 gb ram, = 2gb for virtual and 2-3gb for host)
Create virtual os in software and install!
Then read software help!
Save | Cancel
I notice that this giveaway didn't come in the usual GOTD wrapper. Does this mean that although it comes with the usual "You have to install and activate it before the Giveaway offer for the software is over." warning, that it can be reinstalled at a later date?
Most of us have the same concerns as #3 ric about what happens if you lose encryption software from GOTD in a computer crash, so itt would be great to find out that GOTD and the developer have given us something that can be reinstalled.
Save | Cancel
@ 1 Karl
I see u say many times uninstall via reboot..by that do you mean a virtual program and if so..what program do u use..i'm in need of a virtual program like that..
As for the software here..i've seen and heard of it a few times before..not necessarily here on GOTD but seems to be liked by many...am waiting to see what other comments are made before i install...thas why the question on ur virutal program
Save | Cancel
Again the usual (but important and meaningful) question.
Say for example, I use this giveaway encryption software to encrypt hundreds of important documents.
Then my PC crashed due to malware and this giveaway software was damaged by the crash.
Due to the 1 day expiry limit, this GOTD software cannot be re-installed.
Say good bye to the hundreds of important documents.
Oh, wait. There is a way. Quickly shell out US$30 to buy the software. If the software company has closed and is no longer in business (like so many others)and you cannot even buy it online or at the software retail store, then you are in trouble.
Save | Cancel
ric...you can re-install a freely available 'free copy' that will decrypt your files at anytime if your software gets corrupted.
Save | Cancel
up until now i have been using the serial safe released her on giveawayof the day. but i like this one so much better it is more stable and reliable and the exes it creates are independent of the program itself. and tools like universal extractor cann not be used to by pass the password. the only downside is the created exes arent a choose a file to extract things. cheers
Save | Cancel
Installed and registered without problems on a Win 8.1 Pro 64 bit system.
A company without name and address and the nice remark :
The best way to contact us is via e-mail. ... ooops this is the ONLY way. A name in the software : Serhiy Horobets.
The software installs a passwordgenerator and the encryption engine, which is started via the right-click option. There you'll find a secure erase, an option for self-decrypting . exe files, and the encryption itself.
You can select different encryption methods from AES256 over Blowfish to the old DES. This is of no real use, but if you prefer Blowfish... why not.
The encryption is done fast, the strength of the created keyword is not checked and the way of the encryption behind is hidden. And here we are:
This is surely a good program for the home encrypter to hide information of the husbands or friends eyes. You can safely send messages over the internet to other persons, excluding the NSA...
For real sensitive data, I would never use closed software from a small unknown company. And I would never use software, where I cannot decrypt a file, when I have lost the GOATD registration. And I would never use software in an early programming stage. And I would never...
A long list.
Use this software for your private home computer. It works as it claims without problems. If you have company relevant documents to hide, you are surely informed about the rules, that were setup by the company IT department. These do not include today's software.
Uninstalled via reboot
Save | Cancel