Every day we offer FREE licensed software you’d have to buy otherwise.

Giveaway of the day — Hard Disk Sentinel Standard 5.30
Hard Disk Sentinel Standard 5.30 was available as a giveaway on July 24, 2019!
Detect Hard Drive Issues Before Catastrophe Strikes. With Hard Disk Sentinel, you'll always have a complete overview of your hard disk drive's health, so you can spot potential problems before they result in an irrecoverable data catastrophe. Hard Disk Sentinel is your key to identifying, testing, diagnosing, and repairing hard drive problems, even with Solid State Drives.
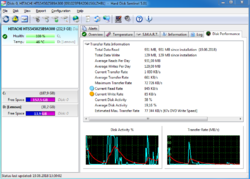
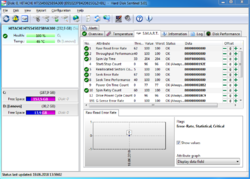
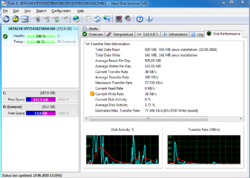
With Hard Disk Sentinel, you can instantly see reports detailing the total health of your drive, including temperature, self-monitoring data, transfer speeds, and more. Any deviation in these factors could be an early warning sign of impending drive failure! Hard Disk Sentinel also works on hard disks that are being used in external USB or e-SATA enclosures and RAID controllers. No need to use separate tools to verify internal hard disks, external hard disks, SSDs, disks in RAID arrays as these are all included in a single software. If your data is important, you owe it to yourself to get a copy of Hard Disk Sentinel today!
NB: For those who have 'file corrupted' error:
This problem is due to our software wrapper that limits the program activation to 24 hours. In this case, you may try using the following:
1) disable the anti-virus suite and restart the computer. You need to disable all the anti-virus systems if you have more than one installed. Make sure it won't start automatically with the computer.
2) download the program archive once again and extract the contents to a dedicated folder
3) carefully follow the installation instructions in the readme.txt file.
4) please mind that all the files have been checked for viruses before the program goes live, so you can be sure that the installer is 100% clean.
System Requirements:
Windows 95/ 98/ 98 SE/ ME/ NT4/ 2000/ XP/ 2003/ 2008/ Vista/ 7/ Home Server/ 2012/ 8/ 8.1/ 10; Pentium or compatible CPU; 64 MB of system memory; HD: 30 MB
Publisher:
Hard Disk MonitoringHomepage:
http://www.hdsentinel.com/hard_disk_sentinel.phpFile Size:
26.9 MB
Price:
$19.50
Featured titles by Hard Disk Monitoring

Order Hard Disk Sentinel PRO with 45% discount for 1 computer, OR for 5 computers, Family license.
GIVEAWAY download basket
Comments on Hard Disk Sentinel Standard 5.30
Please add a comment explaining the reason behind your vote.


Downloaded the free trial on the 24th, but it was asking for a registration key to activate it!? How do I go about getting the registration key? Thanks.
Save | Cancel
Downloaded and installed without a problem...It works exactly as described...Brilliant !!... Still time guys download and install asap
Save | Cancel
Seriously Apart form an AntiVirus/Malware program The HDS Pro Version is the very next thing people should buy and install.
I've bought 3x Family Licenses (1x Given to a good Friend, 1x given to an Relative & one for my home useage).
Of course even v5.40 could use a tweak or two, BUT - You'll NEVER REGRET Buying a HDS Pro License.
Disclaimer: I'm NOT Paid to spruik (promote) the product, but as a paid license owner, I just love what it does including giving PEACE-OF-MiND, and find it THE MOST iNVALUABLE TOOL for a WiNDOWS PC
Save | Cancel
Be sure to poke around in configuration/preferences. Lots of settings.
Save | Cancel
Smooth, problem-free install on Win 10. Thanks...
Save | Cancel
when I download the zip, it only contains the GAOTD installer, not Hard Disk Sentinel. What's going wrong?
Save | Cancel
installed without a problem,
Thank you!
Save | Cancel
I like HDS. Thumbs up !
Save | Cancel
An excellent program, very easy to install. I have used it a year or more. With four HDD of different ages installed it is essentiel to know the condition, teperature etc. HDS solve this the best way.
Save | Cancel
I originally got this as a giveaway, and liked it enough to buy the lifetime "Family Pro 5 pack" and installed it on every machine here.
Just a really good unobtrusive program to keep an eye on your disks and even display the internal temperature of all the drives in the system on your taskbar (if you so wish). My Pro version displays total on time and data written (and total start/stop count for spinning disks) and even predicts life expectancy for every drive it can see on your machine. Plus it will do all kinds of disk tests, both non-destructive (all data is maintained) and destructive (all data is overwritten).
Current Pro version is 5.5, just recently updated.
I have recommended this to friends and business associates.
Save | Cancel
Can we see somewhere the differences between Professional and Standard versions?
Save | Cancel
Seems to work, can be very useful. Thanks~~ win 10x64
Save | Cancel
I have the programme on my XP computer, but since it says it works on Win 98 I downloaded the zip and transferred it to my 98 computer (which is not connected to the internet and has no anti-virus) where I unzipped it and read the readme.
I then pressed setup.exe and a message appeared that setup.exe needs a later version of Windows! (and asks me to upgrade my windows).
I specifically want win98 and nothing later on that computer. Either it does work on win 98 or it does not, why mislead people and waste their time?
Save | Cancel
I haven't used Win 98 for years. There maybe a compatibility mode available when your right-click on the shortcut.
Save | Cancel
Installs ok on one W10 PC but not on another (both ver.1903)- "Activating > Giveaway of the Day > failed to connect."
Both only use Windows Defender.
Save | Cancel
That sounds like an internet problem - "failed to connect"
Save | Cancel
Do yourself a favor and buy the professional version, particularly if you have any spinning hard drives.
Reasons:
1. The professional version of the software will not only alert you if a drive is going bad, but can also email you (I have not tried this feature).
2. You can do a surface test using a variety of methods, which can find and even rescue the data from bad sectors. ONE of the methods is not destructive - after overwriting a sector to test it, it puts the data back, so you don't lose it. I do this on every new hard drive in order to weed out any bad drives before putting them into service.
3. Support is excellent. The author of the software responds quickly to issues. I had a new Kingston drive that was reported as being at the end of life, based on the data it reports. It turns out that the way Kingston reports lifespan in its SMART data is different than most. When I emailed the author about this, he fixed the problem within a couple days.
This software has saved my bacon several times, and is the first piece of software I install on the computers I operate.
Save | Cancel
S. Pupp, Agree with you. The program warned me about an external HD. It was down to 42%. I immediately made a backup. 3 days later it stopped working. Saved me a lot of jobs.
Save | Cancel
Saved more than one of my drives too!
Save | Cancel
This is a good app that I primarily use to monitor conventional hard drive temps when using a USB drive dock -- without active cooling [i.e. a fan] they can get hot enough to become unreliable &/or damage the drive. It does a lot of other stuff too, but for a quick review of S.M.A.R.T. data the free, portable Crystal Disk Info is lighter weight, e.g. quicker to start up & close. I use CPUID HWMonitor for CPU temp & %, & it also shows internal drive temps, so while the taskbar display of temps that Hard Disk Sentinel provides is nice, for me it's unneeded.
Save | Cancel
Installer doesn't errrr actually install the program, but says it has been activated successfully!!! Total waste of time.
Save | Cancel
Datsun, IMPORTANT: Please note that due to the software wrapper, developed by GOTD Team, that limits software ativation to 24 hours only, your installation might be blocked by your antivirus (AVG, Avast or Kaspersky)!
In order to install the program, you'll have to temporally disable your antivirus.
If you have Kaspersky antivirus, please disable it and restart the computer.
Please make sure it won't start automatically with the computer.
Now please download the program archive once again and try to install it.
Be sure, all installers are always tested on virustotal.com and are virus free.
We apologize for inconvenience!
Save | Cancel
Alexa, I am perfectly aware of everything you say, as i have been using software from your site for years, normally without issue. However today, this is not working. I stand by what i said earlier.
It is not the latest version anyway, so i will leave it. Thanks
Save | Cancel
It seems the latest version is 5.50, not this one
Save | Cancel
frank, where does it say that I said it's a waste of time ? I was merely stating fact . And who says the Pope is infallible ?
Save | Cancel
frank, It wasn't Mark, it was me that said it was a waste of time.....credit where it's due!!
Save | Cancel
Is this any different to version 4.71 that was a giveaway more than 2 years ago ?
Save | Cancel
Mark Campbell, You have to read here: https://www.hdsentinel.com/rev_previous_versions.php
Save | Cancel
This is great Hungarian software. I'm proud of my compatriots who created it! :)
Save | Cancel
frank, Then it's time to expand your knowledge!
https://hu.wikipedia.org/wiki/Kateg%C3%B3ria:Magyar_feltal%C3%A1l%C3%B3k
Save | Cancel
For the first time, a program from GOTD fails to install. Says "Failed to Launch the Program."
Save | Cancel
Actually use the free one you get after the premium trail ends. Not bad software at all but I mostly use it to see my drive temps in storage tray. If you own a M.2 drive something like this can be very handy. As for monitoring beyond just generic read/write totals it doesn't have much to offer in terms of drive life. A lot of software out there for this kinda thing but in reality they all have a limited usefulness.
Bad sectors can give you a heads up if something is wrong but most drives never show any odd behavior/symptoms before they crash putting into question the usefulness of all software of this type. The software at it's core just reads total hours/boot cycles/reads writes and compares it to the frequency at which most drives crash under those same conditions to give a fair estimate of life left in the drive.
Save | Cancel
Clinton,
"... I mostly use it to see my drive temps in storage tray. If you own a M.2 drive something like this can be very handy."
FWIW... While it won't work for drives connected via USB, I find CPUID HWMonitor handier since it shows some system data as well. I've also used its drive tests on occasion & found them useful.
Save | Cancel
For regular user it is not easy task to disable Windows Defender on Windows 10. There is no more option to turn it off on settings. Windows 10 Pro users can use "gpedit" to disable it. However Home version does not have "gpedit" function. There is a workaround to add "gpedit" function to Home version. You have to google it, if you want to do it.
j.
Save | Cancel
Jermin,
"... it is not easy task to disable Windows Defender on Windows 10. There is no more option to turn it off on settings. Windows 10 Pro users can use "gpedit" to disable it."
windowscentral[.]com/how-permanently-disable-windows-defender-windows-10
FWIW also check the running processes when Defender's turned off. It's been quite a while, but when I checked win10 ran another, lighter weight Windows security app/process instead. That's one of the things that prompted me to install 3rd party security software that could be turned on/off, but that solution won't work today with 1903 -- Defender will turn itself off when you have other security software installed, but now it will turn back on if that software is either not running or has not been updated.
Save | Cancel
been using the Pro version of HDS for years...works great,never had a problem
Save | Cancel
This is a well-established program with a good reputation. If all you want to do is keep an eye on the temperature of your main drive, it's more than you need, but it's excellent if you're interested in lots of details.
Save | Cancel
I don’t like at all to disable the anti-virus program, though it has been necessary if you should download software from GOTD, and I don’t know why. Can someone tell me? It is a potensially hazard, and for myself I don’t download software from GODT any more, if it is not from a developer Ii really trust.
Save | Cancel
Kjell, though all the anti-virus programs operate on the basis of data that they have collected from constant research over a period of time, that data need not be comprehensive. since thousands of programs (from all types of resources/sources) flood the software domain every day. In order to be effective and used extensively, the a-v programs adopt the principle of "guilty unless proved innocent" and that is the reason you get the warnings from those programs. The a-v programs themselves call these "false positives" .......... From whatever I have experienced, the downloads have not been prevented, but the installations have been. One method that I have used is to disable the a-v programs for 10 mins, download and install and re-enable the a-v. The a-v programs themselves have this feature of limited time non-deployment.... Your method of using the software only from the trusted sources is the best, but others are not that dangerous ....
Save | Cancel
Kjell, most software of this type has to hook into the operating system to function correctly. Malware does the same thing and if it manages to do so than it becomes a lot harder to detect and remove. For this reason several anti-malware programs absolutely reject virtually any program that attempt to do this regardless of reason. In generally it's not a good idea to do this but there is still options to see if it's safe beforehand.
You can always download said program to your computer (with anti-malware software running) than upload the program to virus total to see what they thing about it. Odds are if virus total says the software is clean than it is some antiviruses used can false positive a legitimate program from time to time tho. As long as you do not attempt to run an infected application it really doesn't offer much risk sitting on the drive.
It's only when the program has been launched (at least once) can it do any damage to the system short of a OS exploit where it can auto launch itself (or part of it) and pin itself into the bootloader so it launched on next reboot. This is extremely unlikely even for 99% of malware out there.
Save | Cancel
Kjell,
"I don’t like at all to disable the anti-virus program, though it has been necessary if you should download software from GOTD, and I don’t know why. Can someone tell me?"
1st, it Is Not Always necessary to turn off security software -- I've only had a problem with Defender once or twice, Never had a problem with McAfee, Never with Security Essentials in my win7 VMs, with BitDefender only rarely, & Never with the free version of Kaspersky I ran in a VM for a year. I run the free version of AVG in my XP Pro VM, and I have to turn off real time scanning there to install a GOTD in the wrapper, not because it won't work, but because it slows things down Far Too Much.
Why does some security software object? The methods employed by the GOTD wrapper are also employed by some malware. Windows itself, and all consumer security software make compromises for the sake of usability -- the better your security apparatus, the more inconvenient it is. Some security software presumably doesn't want to compromise when it comes to the GOTD wrapper. And the developers of some security software are no doubt too lazy to try to write code to try to tell the difference between the GOTD wrapper & malware. Then there's also Virus Total... many [most?] security software companies automatically add detection for any new malware uploaded to that database, because you always want the latest protection ASAP, and they only check out those new additions later on. I *think* that's why software like BitDefender occasionally will block the GOTD wrapper, but then will return to normal a day or so later.
Save | Cancel
Clinton,
" As long as you do not attempt to run an infected application it really doesn't offer much risk sitting on the drive."
I'd politely add: *Usually*. There have been cases where malware code runs because of the way Windows itself will look at or examine certain types of files, e.g. .zip files or images. They even figured out how to successfully run malware from emails that Did Not require those emails to be opened.
"... short of a OS exploit where it can auto launch itself (or part of it) and pin itself into the bootloader so it launched on next reboot. This is extremely unlikely even for 99% of malware out there."
Yes, it's less likely today, but not because it's difficult, but because there's so much low hanging fruit that many cybercriminals & would-be cybercriminals don't feel that they have to bother. There are actually more ways than ever before to ensure persistence [as it's called]. The latest frontier so-to-speak seems to be the sort of mini OS used by UEFI BIOS -- they found an early-on example of UEFI malware in the wild a while back, and they've likely only gotten better at it since.
Be Careful Out There.
Save | Cancel
Clinton,
>"short of a OS exploit where it can auto launch itself (or part of it)"
It is impossible for any program to auto launch itself; programs cannot think or make decisions on their own. That occurs only after they are loaded into a running state. The CPU then processes the steps in the program, which could then do lots of good or bad things. The main point is that a program has to be started by some other running program or the (already running) operating system.
I purchased the HDD Sentinel program several years ago. I am not aware of it hooking itself into the operating system in a manner that it cannot be uninstalled.
Save | Cancel
Kjell,
>"I don’t like at all to disable the anti-virus program, though it has been necessary if you should download software from GOTD, and I don’t know why. Can someone tell me?"
It isn't GOTD's fault. I have never had to disable my anti-virus program to install any program from GOTD, and I have successfully installed hundreds over the years. Some anti-virus software will view the setup used for most GOTD offers and block it. Most anti-virus software also have a method to allow programs you specify as safe, but very few people ever bother to go and make the change. Over the years, the same question you have asked has been asked by others. After learning they can alter their anti-virus settings, they have not had any more problems. Take a look and see if that will help you.
Save | Cancel
TK,
>"Gary, not strictly true there have been and will be many cases of remote code execution vulnerbilities including some that were designed in like the .WMF remote code exectuion vulnerability"
Yes, other than the user initiating a program to execute (via the OS, scheduler, or anything that causes the file to be processed by the CPU), there have been many different types of initiating a program to execute, from the early days of DOS and ASCII BOMBs (sending a text file to the screen could cause a program to start) to the e-mail attachment vulnerabilities we had just a few years ago (assessing (not accessing) the attachment could cause a vulnerability). Executables have been hidden in all types of files, and then a method was used to start the executable part (e.g., an image viewer displaying a photo, and the processing of displaying the photo triggers something being loaded into executable memory). Those sort of vulnerabilities get solved pretty quickly.
Steve Gibson's coverage of the Microsoft MICE issue was big news back in 2010 (I think)(before Vista). I have not found any machines in a long time that originally had it because any that did have all probably been patched. Later machines didn't have it because it was removed by Microsoft. Even the MICE issue required something else processing the meta file before it caused an execution.
The main point is that regardless of what type of file (standard executable/hidden/disguised. etc.) it is merely taking up space on disk (non active), and cannot start itself. Something else has to trigger the action that causes that file to be processed in some manner before it will execute or cause something else to execute.
Save | Cancel
TK,
You are pointing out more possibilities of vulnerabilities, and the ones you mention only skim the surface of what types of exploits that have been developed, ... but my initial comment has nothing to do with those possible vulnerabilities. I was responding to part of the comment made by Clinton, which contained the text:
>"short of a OS exploit where it can auto launch itself (or part of it)"
That part I quoted at the start of my comment. Had I thought of it, I would have shortened my quoted text back to him to:
>"... where it can auto launch itself ..."
The only part of that comment I was responding to is the part about a program/exploit auto launching itself. Nothing on the computer can auto launch itself, not even the OS. It needs the BIOS to initiate the OS. The BIOS needs the circuitry/logic to start it when power is applied.
Clinton's comment just above that line I quoted said essentially the same thing: "As long as you do not attempt to run an infected application it really doesn't offer much risk sitting on the drive."
The part of a program "auto loading itself" is what I wanted to clarify. That part of the comment seemed to contradict the statement he had just made. I think if Clinton thought about it, the sentence would be worded slightly different. Anyone that knows very much about how a computer works (and obviously Clinton does) knows that executable code has to started by something that is already executing, whether it be initiated by the user telling the OS to start it, a scheduler that the OS runs that will start it, or a remote execution that starts it. The main point is that it cannot start itself; some already executing code must initiate it. I am pretty sure that is what Clinton was intending to point out as well. It just seemed odd to use the "auto load itself" part. It makes it sound like a file could somehow spontaneously start itself. For anyone that might have thought that was possible, I just wanted to make that part clear.
Save | Cancel